We tested the throughput of the device login certification and the effect was relatively satisfactory.Because we did not have more than 1,000 devices that would connect to the server at the same time.
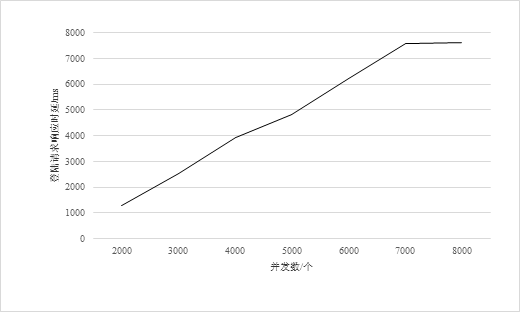
We tested the throughput of the device login certification and the effect was relatively satisfactory.Because we did not have more than 1,000 devices that would connect to the server at the same time.
